How to bypass the credential manager in Windows
A method to escalate your privileges without knowing any password.

Hi guys!
Recently I took a course about windows privilege escalation, and today I want to show you a very cool method that you can use to escalate your privilege without knowing the password of the user account.
Let’s start!
Windows credential manager
First, if you don’t know what windows credential manager is, it’s just a simple password manager pre-installed in windows where you can save your credentials both for user and websites.

So basically you can save your password in 4 different sections.
- Windows credentials that are used by windows.
- Certificate-Based Credentials as the name say use certificates, however they are pretty rare to use.
- Generic credentials.
- Web credentials used for saving logins for websites.
Now let’see how we can save our credentials.
Open the search bar and type Credentials manager.


Now let’s try to add a new credential.



We can confirm that the credential has been saved by run the command below.
cmdkey /listNote: cmdkey is a command line tool that allows you to create, delete and list saved credentials.


Perfect, the next step is to download this empire script.
Empire/dumpCredStore.ps1 at master · EmpireProject/Empire · GitHub
This tool uses a set of windows32 APIs to retrieve information about all the saved credentials.
Here is the page with documentation of those APIs if you are interested.
Now all you have to do is run this command.
powershell Import-module <File-Path> ; Enum-Creds

Note: Sometimes is possible that you can obtain an error say that the PowerShell file cannot be executed due to the execution policy, to avoid that type the command below in the cmd.
powershell Set-ExecutionPolicy -Scope CurrentUser UnrestrictedAnd finally, here are our passwords 🥳.
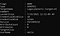

Now that we know the password for that user, all we need to do is just run the command runas to run commands as that user.
runas /user:<USER> <YOUR_COMMANDS>Note: runas is used to run tools or commands with different privileges, impersonating another users.


Hope you guys learned something new today.
Have a great day, bye!'
THANKS TO : -

